Leveraging the Possibilities of Ray Serve in Implementing a Scalable, Fully Automated Digital Verification Service
Tanja Bayer is a machine learning engineer at cidaas, where she and her colleagues work on a fully automated video identification service
 The cidaas ID validator provides online verification of ID cards with the help of artificial intelligence.
The cidaas ID validator provides online verification of ID cards with the help of artificial intelligence. This blog takes a closer look at digital identity verification, especially in the context of the cidaas ID validator and the modern Cloud Identity & Access Management solution – cidaas. You will get insight into what digital identity verification actually is, which concepts and technologies are used, and how Ray Serve has enabled us to implement an architecture that has increased the processing of our service by an approximate factor of four.
LinkWhat is Authentication and Identity Verification?
The cidaas identity platform provides feature-complete Identity & Access Management, including an extensive set of authentication methods. A normal user regularly authenticates themselves on various digital services and apps, using a login with username and password or passwordless login via device biometrics such as FaceID or TouchID. Thus, authentication is basically the verification of a user or in some use cases also a device in a process or in an application.
Identity verification in also verifying the identity of the user to ensure that the user is who they claim to be. An identity verification is usually performed based on identity documents, e.g. an ID card, a passport or even a driver's license. Identity Verification is often required when an identity proof is required by legal regulations or security and compliance guidelines, e.g. signing contracts online, or digital onboarding of persons to classified content.
The cidaas ID validator offers a fully automated digital identity verification process with which identity documents can be easily verified. The identity verification is quite simple: the user records videos of the identity documents and their face in a guided process with clear instructions. To verify the user’s identity, the cidaas ID validator uses artificial intelligence to compare biometric data of the ID document and the real person, check the security features of the ID document, as well as do a liveness detection and a real-time check.
Note, the cidaas ID validator complies with the highest European standards for digital identification according to eIDAS.
LinkThe solution architecture of the cidaas ID validator
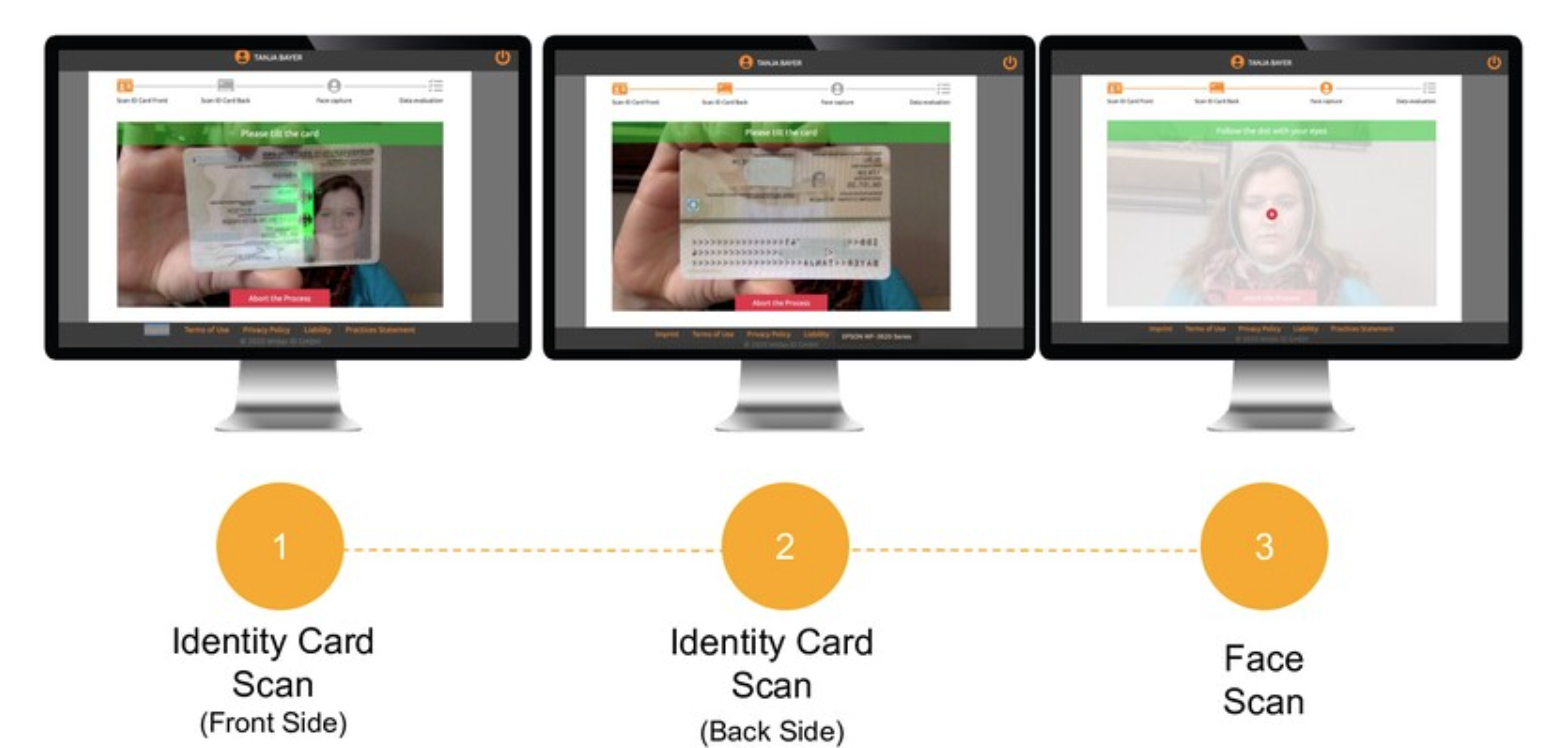
The data gathered and used in the cidaas ID validator while performing an identity verification process results from three different input streams in case of an ID card.
The face scan and user interaction
Front side of the ID card
Back side of the ID card
Thus, the three input streams match the three steps of the identity verification process of the cidaas ID validator. In the first step the user interacts with the system to scan the face of the person and make sure the process is performed by a real person and not a video replay. In the second step the front side of the ID card is recorded, and the security features and further details are extracted from the ID card. In the last step, the back side of the ID card is recorded, and further details and security features are extracted.
During the process, the data on the ID card and the person is analyzed, and several checks are conducted. As a high-level summary, the following criteria are important:
Is a real person performing the identity verification process?
Does the data on the identity document match the person who initiated the process, e.g., does the name and birthdate match?
Is the data on the identity document valid?
Does the person who performs the identity verification process match the person on the identity document?
And of course, is the identity document a valid document, without manipulation and with proper security features?
The criteria are considered and evaluated by different models and are combined to deliver a result on the question, “Is it a valid identity verification process, conducted with a proper identity document and performed by the matching person in real time?”
The basic criteria listed above, together with the fact that the identity verification process is based on a combination of several input streams and several models which correlate, lead to certain implications for the architecture.
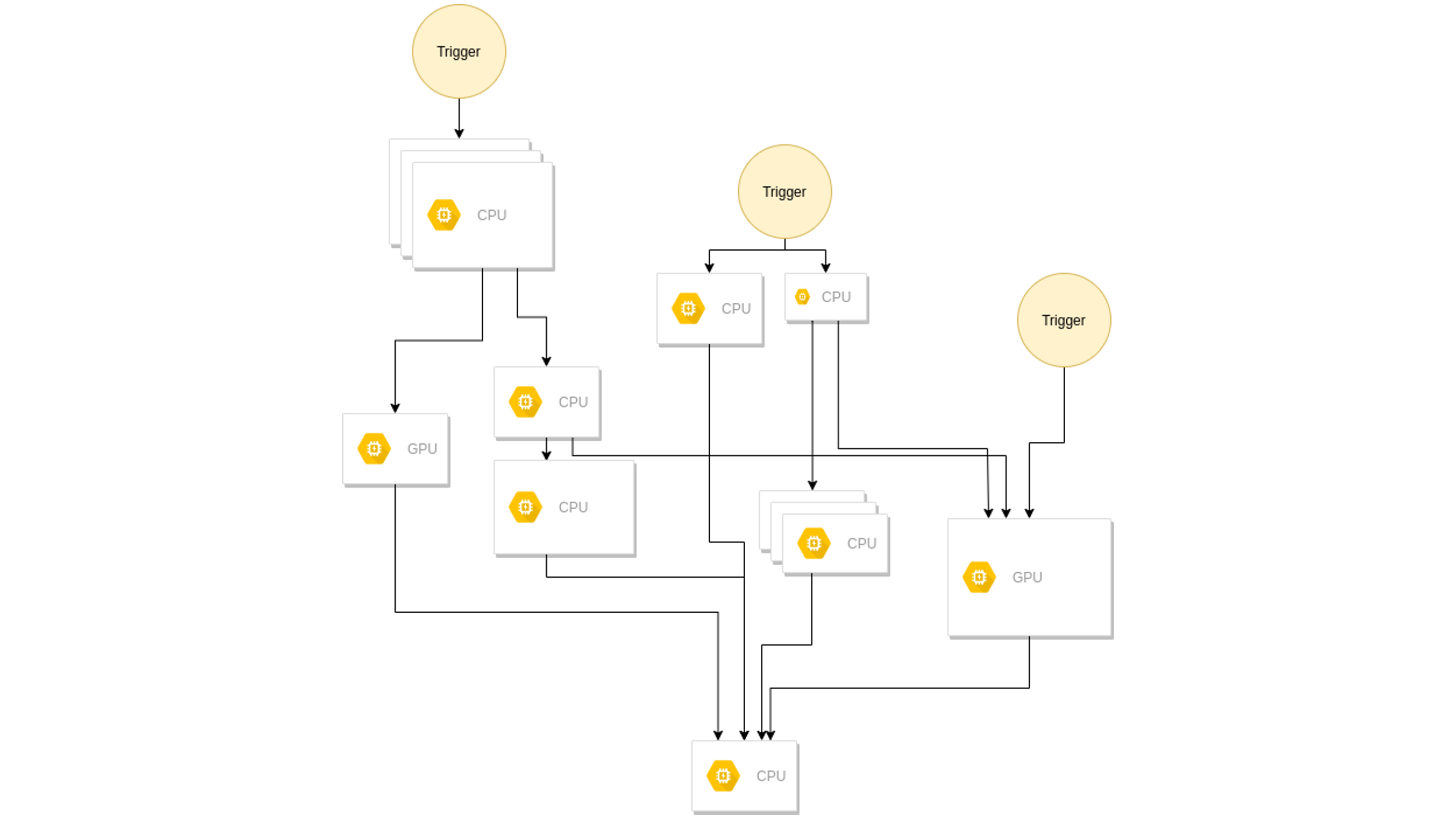
Most of the data handled in the identity verification process is image and video data, which involves common computer vision algorithms as well as different machine learning models while processing. A split into small tasks processed in a graph and event-based architecture was required to achieve a scalable and performant architecture. Due to the correlation of the different tasks and the computing time difference of the independent tasks – the event-based architecture was most suitable to resolve the correlation and avoid blocking states or processes.
LinkHow we utilize Ray to get production ready and distribute computing
To move from a proof-of-concept state to production-ready, several requirements were gathered to decide which platform will meet all requirements and should be used as underlying infrastructure.
Based on our need to split tasks, distributed and parallel processing was essential.
With the rollout of the cidaas ID validator for millions of users, the scalability of the platform is important to achieve great performance and ensure long-term growth.
Handling of large data is crucial – considering the combination of image and video data and the millions of users on the platform results in a large amount of data.
Support for Python, as one of the most common languages in data science, as well as a good support for integrating machine learning models.
Last, but not least, we also took community adoption and the open-source mindset into consideration.
After evaluating these requirements as well as different platforms, we decided Ray Serve was the perfect platform to implement the cidaas ID validator.
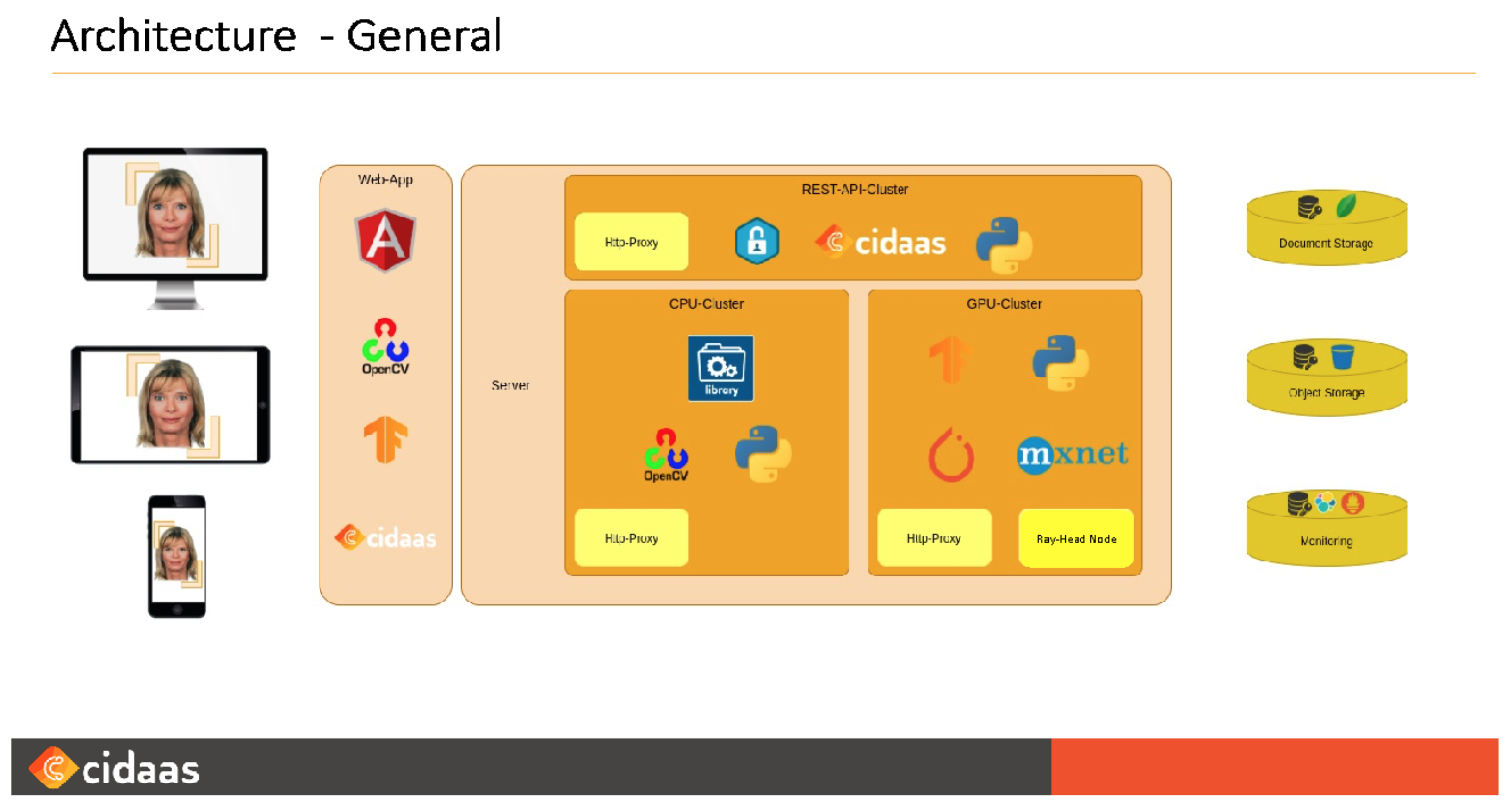
Let’s take a look at the final architecture of the cidaas ID validator based on Ray Serve. A cluster setup was created to ensure the best balance between speed and resources.
The Backend was split into three different clusters. First, there is the CPU Cluster which performs most of the computer vision tasks, as well as some preprocessing tasks required for the Machine Learning Models.
One note people might come across when implementing computer vision algorithms is the support of multiprocessing which only some libraries provide. However, many computer vision libraries are not built for running multiple copies on the same machines. Some libraries will default to use all the cores on the machine, this can become problematic when Ray runs many replicas of the models in different processes. Ray already makes some effort by setting the OMP_NUM_THREADS=1 variable which is a standard across parallelization libraries. However, there might be libraries that don't honor this variable and have specific options you need to set to constrain the parallelism within a process.
Second, the GPU cluster contains all backend services to run Machine Learning Models. This cluster also contains the head node. Since the CPU load on this cluster is simple to predict, all the GPU backends run iteratively task by task, and so the CPU nodes on this cluster are not overloaded. Hence, it was easy to ensure that this cluster is never occupied 100%, thereby making sure that the performance of the Ray head node processes is not affected.
Additionally, the GPU cluster is also used to start all Ray Serve deployment services. This means, no additional logic is required to check if the head is up.
Finally, we have the API cluster with the main focus on high availability. The API cluster needs to serve the request from the cidaas ID validator UI instantly as well as take care of the Global Data Actors. The Global Data Actors are used to sync the different tasks and handle asynchronous events which result from the event-based architecture, splitting the process into small tasks as well as the distributed and parallel processing.
LinkSummary
Ray and Ray Serve has provided an easy way to scale up our services, reduced the number of frameworks used, and has lowered the effort required for maintenance. Perhaps most importantly, it has enabled us to implement an architecture that speeds up the processing of our service by an approximate factor of four.
All this is essential to provide the best identity verification service –cidaas ID validator.


